In the realm of access control, a revolution is underway. The key to this revolution is a technology known as Radio Frequency Identification, or RFID.
RFID technology is not new. It has been around for decades. But its applications are expanding rapidly, particularly in the field of access control.
At the heart of this technology is the radio frequency ID card. This small, unassuming piece of plastic is transforming how we secure our spaces. It's making access control more efficient, more secure, and more adaptable than ever before.
But what exactly is a radio frequency ID card? How does it work? And why is it so effective for access control?
A radio frequency ID card, or RFID ID, is a type of smart card. It contains an embedded RFID chip. This chip can store a significant amount of data.
The data on the RFID chip can be read by an RFID reader. This is done wirelessly, using radio waves. The reader can then use this data to determine whether to grant or deny access.
This process is fast and automatic. It doesn't require the card to be physically inserted into a reader. In fact, the card doesn't even need to be taken out of a wallet or purse.
This makes RFID ID cards incredibly convenient. But convenience is just the beginning. These cards also offer a high level of security.
The data on an RFID chip can be encrypted. This makes it difficult for unauthorized individuals to read or alter the data. Furthermore, the data can be updated or changed as needed, providing a dynamic and flexible solution for access control.
RFID ID cards are also highly versatile. They can be used for a wide range of applications, from securing buildings to tracking inventory. This versatility, combined with their convenience and security, is why RFID ID cards are becoming the go-to solution for access control.
But as with any technology, RFID is not without its challenges. There are concerns about privacy and security. There are also technical considerations, such as the need to integrate RFID systems with existing infrastructure.
Despite these challenges, the future of RFID in access control looks bright. Innovations are continually emerging, pushing the boundaries of what this technology can do.
So, are you ready to discover the future of access control? Are you ready to delve into the world of radio frequency ID cards? If so, then read on. This article will guide you through the ins and outs of RFID technology, its applications, and its future prospects.
Introduction
What is RFID?
Radio Frequency Identification, commonly abbreviated as RFID, is a form of wireless communication. It uses electromagnetic fields to identify and track objects automatically. This technology is remarkably versatile, offering a wide array of applications across industries. Central to RFID are the small tags attached to items, which contain unique identifiers. These tags communicate with RFID readers, devices that can detect and read the information stored on the tags. This seamless interaction happens without physical contact, enhancing convenience.
RFID technology is part of everyday life, yet often goes unnoticed. From tracking products in a warehouse to speeding up transactions in stores, RFID plays a crucial role. It's a cornerstone of automation and efficiency in many sectors today.
Definition of Radio Frequency Identification
Radio Frequency Identification operates through a system comprised of several key components. These include RFID tags, RFID readers, and an antenna. The technology allows for the transmission of information between a tag and a reader using radio waves.
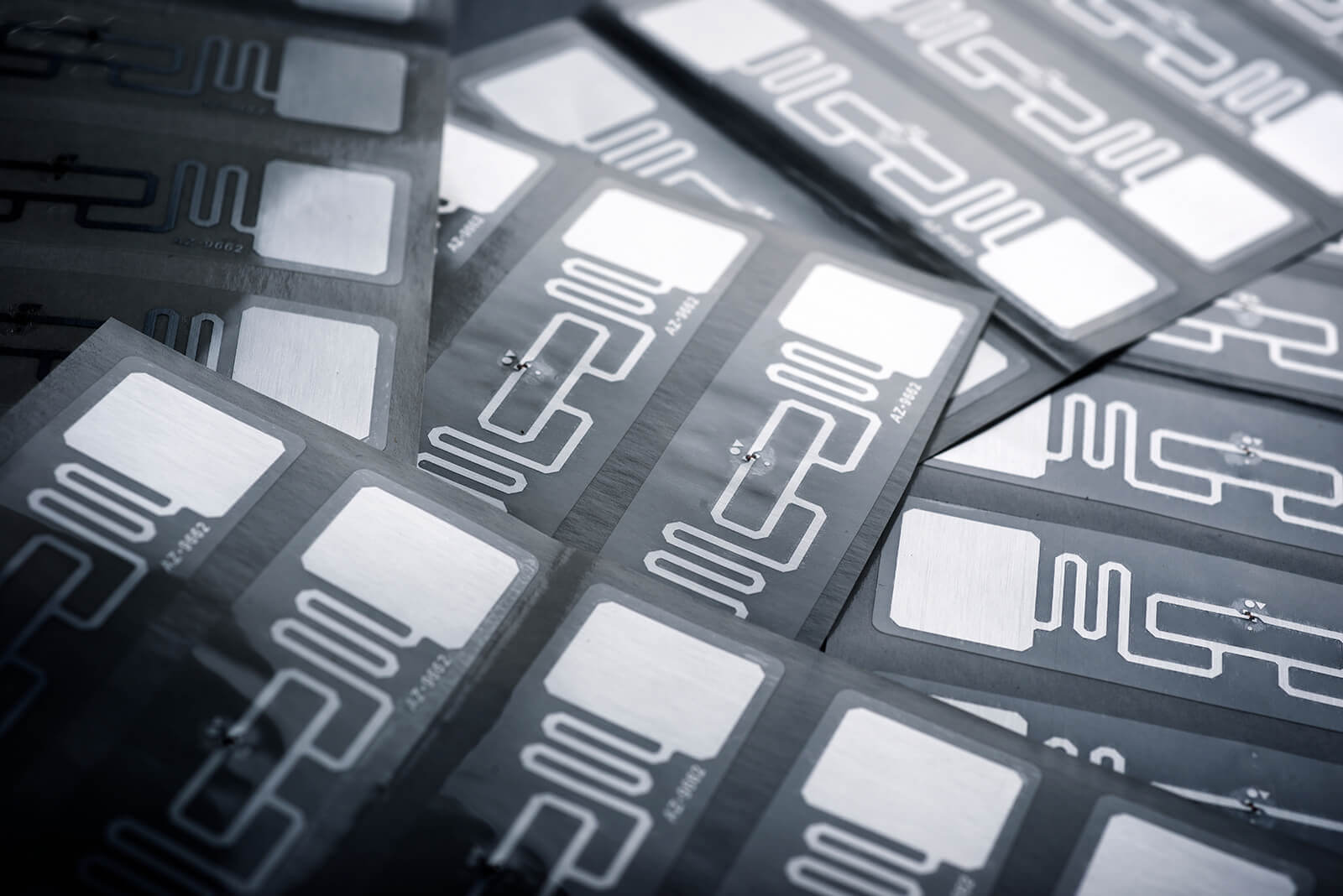
An RFID tag comprises a microchip with memory and an antenna for broadcasting signals. These tags can be passive, active, or battery-assisted passive. Passive tags are powered by the reader's signal, while active tags have their own power source, allowing for greater range.
The data exchanged between the reader and tag enables identification and tracking. This is executed almost instantaneously, boosting efficiency significantly. RFID systems can operate at different frequencies, each suitable for various applications ranging from inventory management to access control.
In essence, RFID technology simplifies processes by providing a robust method for automatic data collection and asset tracking. Its ability to identify objects without direct line-of-sight gives it an edge over traditional barcodes. This makes RFID an indispensable tool in modern logistics and security systems.
How Does RFID Work?
The Role of RFID Chips
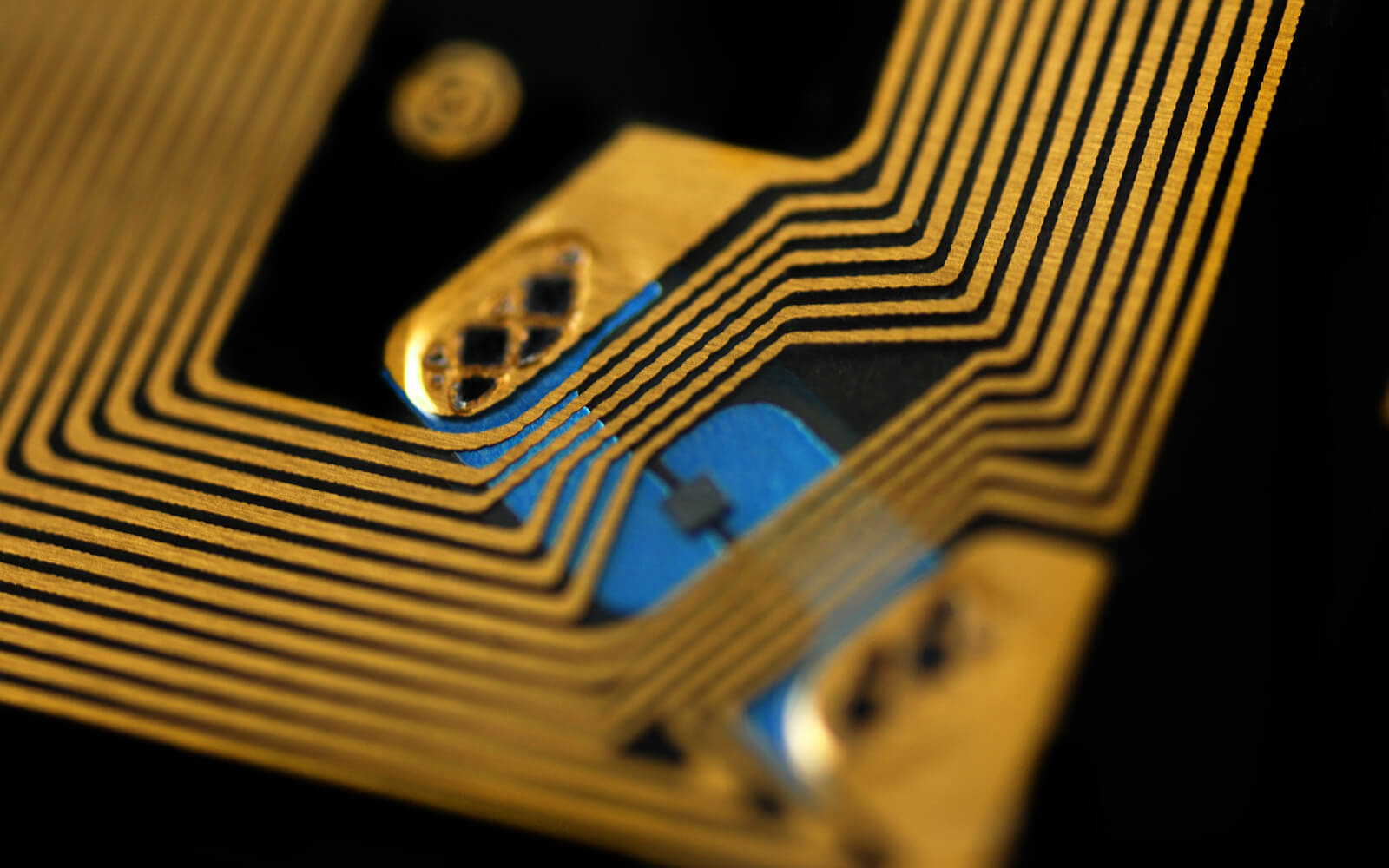
At the heart of each RFID system lies the RFID chip. This small yet powerful component is crucial for the technology's functionality. It's embedded in RFID tags and stores crucial data for identification and tracking.
RFID chips come in various types, designed for different purposes. Some chips are read-only, meaning their data is set at manufacture and cannot be altered. Others are read-write, allowing data to be modified or updated as needed.
The memory capacity of RFID chips varies, but it's typically enough to contain a unique identification number along with other essential data. This flexibility makes RFID chips suitable for numerous applications, such as access control and inventory management.
Here are some key components of RFID chips:
- Integrated Circuit (IC): This is the brain of the chip, processing data.
- Antenna: Allows the chip to communicate with the RFID reader.
- Substrate: The base material on which the IC and antenna are mounted.
Given these components, RFID chips can execute complex operations. They respond to signals from RFID readers, initiating the exchange of information. This process helps automate many tasks that traditionally required manual effort.
Communication Between RFID Tags and Readers
The interaction between RFID tags and readers is fundamental to how RFID technology works. This communication happens via radio waves, eliminating the need for physical contact. It's what facilitates quick and efficient data exchange.
When an RFID reader sends out a signal, it activates nearby RFID tags. The tags then use their antennae to capture this energy, allowing passive tags to power up and active tags to strengthen their signals. The data stored on the tag's RFID chip is then transmitted back to the reader.
The reader decodes this data and processes it, either through a built-in system or by sending it to a connected network. This information, once collected and analyzed, provides critical insights for various applications.
RFID systems have several advantages due to their unique communication method:
- No line-of-sight required.
- Ability to read multiple tags simultaneously.
- Fast and accurate data collection.
- Diverse range of use, from inventory management to secure access.
Readers can be stationary or mobile, depending on the requirements of the application. Each type offers specific benefits, such as fixed readers for continuous monitoring or handheld readers for flexibility in different settings. Regardless, the seamless connection between tags and readers is what makes RFID a powerful tool in modern technology.
Understanding RFID Tags
What Are RFID Tags Used For?
RFID tags are versatile tools used across various industries, each serving multiple critical functions. Primarily, they facilitate automatic identification and tracking through the use of radio waves. This makes them indispensable in applications ranging from logistics to security.
In inventory management, RFID tags streamline tracking, providing real-time data about stock levels and locations. This reduces errors and enhances efficiency in supply chains. Retail businesses capitalize on this advantage to maintain optimal inventory levels and prevent stockouts.
Access control systems also benefit greatly from RFID technology. By incorporating RFID tags into ID cards, businesses can secure premises and restrict unauthorized access efficiently.
Beyond security, these tags enhance convenience, allowing employees to move quickly through checkpoints without manual verification.
The healthcare sector employs RFID tags for patient monitoring and asset tracking. With RFID technology, patient data can be updated instantly, ensuring accurate information. This supports better patient care and enhances the security of medical equipment.
Key uses for RFID tags include:
- Inventory tracking
- Access control
- Patient monitoring
- Asset management
- Contactless payments
Types of RFID Tags
RFID tags come in various forms, each tailored for specific applications and environments. Their design and functionality depend largely on the energy source used to power them. Understanding these different types helps select the right tag for each need.
Passive RFID tags are the most commonly used due to their cost-effectiveness. They do not contain an internal power source, instead drawing energy from the reader's signal. This limits their read range but makes them ideal for applications like inventory tracking.
Active RFID tags, in contrast, contain a battery, allowing them to transmit signals over greater distances. They are often used in environments where long-range scanning is required, such as in large-scale logistics operations. The added power extends their functionality but at a higher cost.
Battery-assisted passive (BAP) RFID tags combine features of both passive and active tags. They contain a small battery to power the chip, enhancing their signal without constant external power reliance. This makes them versatile for mid-range applications.
Key RFID tag types include:
- Passive RFID tags
- Active RFID tags
- Battery-assisted passive (BAP) RFID tags
Key Components of RFID Tags
Understanding the components of RFID tags illuminates how they function and interact with readers. Each component plays a vital role in data storage and communication processes, ensuring efficient performance.
The integrated circuit (IC) is often referred to as the brain of the RFID tag. It manages the data processing and facilitates communication with the reader. This small chip can store unique identifiers and additional data necessary for specific applications.
The antenna is another crucial component, enabling the tag to receive and send radio signals. Its design and size affect the tag's performance, particularly the read range and speed. Ensuring the proper antenna configuration is vital for optimal functionality.
The substrate serves as the foundational layer that holds the components together, providing structural integrity. Its material affects the tag's flexibility and durability, which are important considerations for different application environments.
These components together form the core of RFID technology, enabling seamless operations across a range of industries. Whether tracking assets or securing locations, each part plays a pivotal role in ensuring RFID systems function effectively.
The Benefits of RFID in Access Control
Enhanced Security Measures
RFID technology offers unparalleled security enhancements, fundamentally transforming access control systems. By using radio frequency identification, organizations can safeguard restricted areas more effectively. RFID-enabled ID cards are instrumental in verifying user identities quickly and accurately.
Encryption plays a significant role in the security of RFID systems. Advanced encryption protocols protect data stored on RFID cards, minimizing unauthorized access. This means sensitive information remains secure even if the card is lost or stolen.
Moreover, RFID systems allow for real-time monitoring and reporting. This ability to track access logs means organizations can instantly detect and respond to security threats. Real-time insights contribute to creating a secure environment, deterring potential unauthorized attempts.
Integrating RFID with other security systems can further strengthen security. Combining RFID with biometrics or smart card technology adds additional verification layers. Such integration provides comprehensive solutions that enhance the security of physical and digital spaces.
Streamlined Processes
RFID technology streamlines a multitude of processes, significantly improving efficiency. In access control, RFID cards reduce the need for manual checks and paperwork. This speeds up entry and exit, enhancing convenience for users.
Organizations benefit greatly from RFID's ability to automate processes. By replacing traditional methods with RFID, they can eliminate bottlenecks and reduce operational costs. This automation of routine tasks allows personnel to focus on more complex responsibilities.
RFID systems also improve data accuracy, which is vital for decision-making. Automatic data capture eliminates human error, ensuring consistent and reliable data. With precise information, organizations can make informed decisions promptly.
Furthermore, RFID technology enables seamless integration with existing systems. This flexibility allows businesses to upgrade their processes without extensive disruptions. By incorporating RFID into current frameworks, companies can enhance capabilities and maintain operational continuity.
Real-time Tracking
The ability to track data in real-time is a standout feature of RFID technology. This capability transforms how organizations manage assets and resources. Real-time tracking ensures that information is always current and accessible for immediate use.
In access control, real-time tracking facilitates swift identification of personnel and assets. Whether monitoring employee movement or securing equipment, RFID delivers accurate location data. This results in enhanced security and optimal resource allocation.
RFID tracking also supports proactive management strategies. By providing instantaneous alerts and notifications, organizations can address issues before they escalate. This proactive approach reduces downtime and mitigates potential risks.
Additionally, real-time tracking enhances transparency in operations. It offers a comprehensive view of activities, contributing to improved oversight and management. This transparency builds trust and accountability, essential for effective governance and compliance.
Overall, the benefits of RFID in access control extend far beyond security. They encompass streamlined processes and real-time insights, offering organizations a robust solution for modern challenges. The integration of RFID technology ensures optimal performance in dynamic environments.
Challenges and Considerations
Security Risks and Solutions
Despite its advantages, RFID technology faces security challenges that need addressing. One major concern is unauthorized scanning, where malicious entities attempt to read RFID tags without permission. This can lead to privacy breaches, with sensitive data being intercepted.
To mitigate unauthorized scanning, organizations can use encryption and authentication protocols. These measures ensure that only authorized RFID readers can access tag information. Encryption acts as a strong deterrent to potential data thieves, preserving the confidentiality of sensitive details.
Another risk involves RFID skimming, where criminals capture data from RFID-enabled cards. This issue calls for enhanced protective measures, such as RFID-blocking sleeves or wallets. These accessories block electromagnetic signals, safeguarding cards against unwanted reads.
Moreover, implementing robust access control policies is crucial. Organizations should regularly audit and update security protocols to address emerging threats. Continuous monitoring and timely response form the cornerstone of effective RFID security strategies, minimizing vulnerabilities.
Integration with Existing Systems
Integrating RFID technology with existing systems presents its own set of challenges. One common issue is compatibility, as legacy systems may not easily accommodate new RFID infrastructure. This can require significant upgrades or adaptations, which may increase costs and time requirements.
To address compatibility, a thorough assessment of current systems is essential. Understanding the intricacies of existing infrastructure aids in planning a seamless RFID integration. This knowledge facilitates the selection of RFID solutions that align with specific organizational needs.
Another consideration is data interoperability, which involves ensuring that new and old systems can communicate effectively. Without proper data translation, information could be lost or corrupted. Middleware solutions can play a vital role, acting as connectors that harmonize diverse data formats.
Furthermore, staff training is vital for successful integration. Employees should understand how to use and manage RFID systems effectively. Comprehensive training programs empower personnel to navigate new technologies confidently, maximizing the benefits of RFID implementation.
In summary, while RFID technology offers numerous benefits, challenges remain in terms of security and integration. Addressing these issues requires proactive strategies, including enhanced encryption, compatibility assessments, and staff training. Such measures ensure RFID systems function optimally, delivering secure and efficient solutions for modern access control needs.
Future Trends in RFID Access Control
Innovations in RFID Technology
RFID technology is evolving rapidly, bringing many innovations to access control. One significant advancement is the development of smaller, more powerful RFID chips. These chips can be integrated into smaller form factors, allowing for greater versatility in application.
Another exciting innovation lies in the area of energy harvesting. New RFID tags can generate energy from ambient sources, reducing the need for battery replacements. This means tags can operate more sustainably in various environments.
Multi-frequency RFID solutions are also gaining traction. These allow tags to operate across different frequency bands, enhancing their versatility. Multi-frequency systems can cater to more diverse needs, offering wider applications in industries like logistics and healthcare.
In addition, security features within RFID systems are improving. Advanced encryption technologies are being incorporated, strengthening defenses against unauthorized access. These enhancements ensure that RFID continues to be a robust choice for secure access control systems.
Predictions for RFID in Security
The future of RFID in security looks promising, driven by continuous technological advances. One prediction is the increasing integration of RFID with biometric systems. Combining these technologies can enhance accuracy in identity verification, strengthening security frameworks.
RFID is also expected to play a more prominent role in the development of smart cities. As urban areas become more connected, RFID will aid in managing infrastructure more efficiently. It can support everything from traffic management to public safety, underscoring its versatility.
Another prediction is the expansion of RFID into wearable technology. With smart wearables becoming more prevalent, RFID tags will likely be used for personal access and security. This can streamline how individuals interact with their environments, from making payments to opening doors.
Furthermore, RFID is anticipated to offer greater customization in security applications. As technology matures, customizable features will allow more tailored security solutions. This flexibility will be crucial in meeting the diverse needs of businesses across different sectors.
In summary, RFID technology is on a path of innovation and expansion. With emerging trends and predictions, its role in security systems will grow more vital. As RFID integrates with other technologies, it will continue to shape the future of access control, offering robust and versatile solutions.
Conclusion
Recap of RFID Benefits
RFID technology has revolutionized access control with its impressive capabilities. By using electromagnetic fields, RFID provides automatic identification and tracking, vastly improving efficiency and accuracy. Unlike traditional methods, RFID does not require line-of-sight, allowing for smoother operations in various settings.
One of the key advantages of RFID lies in its enhanced security features. RFID ID cards can store ample data with encryption and authentication protocols, ensuring secure access to sensitive areas. The integration with other security systems like biometrics further strengthens the reliability of RFID in critical applications.
Moreover, RFID simplifies processes with its ability to handle multiple tags simultaneously. This capability streamlines operations in environments such as warehouses, hospitals, and offices. Businesses and industries experience significant time savings and reduced human errors, resulting in improved overall productivity.
In essence, the benefits of RFID are multifaceted. From heightened security to operational efficiency, RFID provides a robust solution to meet modern access control needs. The continued advancements in RFID technology promise even greater innovations, ensuring its relevance and utility in the years ahead.
RFID in Action: Products & Projects
Curious to see how RFID is transforming access control and beyond? We’ve got you covered.
Explore our range of RFID Click boards™ – ready-to-use modules designed to streamline RFID integration. Ideal for building secure, contactless systems for access control, asset tracking, authentication, and more.
Want to see RFID in action? Dive into real-world projects on EmbeddedWiki. Discover how developers are using RFID technology in smart security systems, automation setups, and IoT applications. Whether you're after fresh ideas or full project tutorials, it’s all just a click away.












 RFid Click
RFid Click  RFID 2 Click
RFID 2 Click  Magic RFID Click
Magic RFID Click  NFC Click
NFC Click  NFC 2 Click
NFC 2 Click  NFC 3 Click
NFC 3 Click  NFC 4 Click
NFC 4 Click NFC 5 Click
NFC 5 Click NFC 6 Click
NFC 6 Click NFC 7 Click - SPI
NFC 7 Click - SPI  NFC 7 Click - I2C
NFC 7 Click - I2C  NFC Tag Click
NFC Tag Click  NFC Tag 2 Click
NFC Tag 2 Click NFC Tag 4 Click
NFC Tag 4 Click  NFC Tag 5 Click
NFC Tag 5 Click  NTAG 5 Link Click
NTAG 5 Link Click  NFC Extend Click
NFC Extend Click 















